You can use the RAM Roles for Service Accounts (RRSA) feature to enforce access control on different pods that are deployed in a cluster. This implements fine-grained API permission control on pods and reduces security risks. This topic describes how to use RRSA.
Background information
OpenID Connect (OIDC) is an authentication protocol that is developed based on Open Authorization (OAuth) 2.0. Alibaba Cloud Resource Access Management (RAM) supports OIDC-based single sign-on (SSO). An application deployed in a Kubernetes cluster can use a Security Token Service (STS) token generated for the RAM role assumed the application pod to call the API operations of cloud services. Alibaba Cloud Container Compute Service (ACS) supports the RRSA feature. In multi-tenant scenarios, you can use the RRSA feature to authorize different pods to access different cloud services. You can use the RRSA feature in ACS clusters to control the validity period of STS tokens.

The following steps show how an application accesses a cloud resource when RRSA is used to enforce access control.
Deploy a pod that has the feature of service account token volume projection enabled.
NoteThe ACS cluster has the feature of service account token volume projection enabled by default.
The ACS cluster creates a service account OpenID Connect (OIDC) token file and mounts the token file to the pod.
The application in the pod uses the OIDC token file to call the AssumeRoleWithOIDC API operation of STS and obtain the STS token that is used to assume a RAM role.
NoteTo enable the application to perform these operations, you must first modify the configuration of the RAM role to authorize the service account used by the pod to assume the specified RAM role. For more information, see AssumeRoleWithOIDC.
The application in the pod uses the STS token to assume the specified RAM role and then calls the API of the relevant cloud service.
Enable RRSA
Log on to the ACS console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side navigation pane of the cluster details page, click Cluster Information.
On the Cluster Information page, click the Basic Information tab. On the Basic Information tab, click Enable RRSA.
In the Enable RRSA message, click Confirm.
NoteIt takes about 2 to 3 minutes to enable RRSA. If the Cluster Status column consistently displays Updating, click
 in the upper-right corner to manually refresh the page.
in the upper-right corner to manually refresh the page. After the cluster status changes from Updating to Running, RRSA is enabled for the cluster. Move the pointer over Enabled to the right of RRSA OIDC to view the URL and ARN of the OIDC provider.
After RRSA is enabled, ACS performs the following operations in the background:
Automatically creates an OIDC issuer that is dedicated to the cluster. The OIDC issuer is managed by ACS.
Creates a RAM role identity provider within your account. The identity provider uses the OIDC issuer for single sign-on (SSO). The identity provider is named ack-rrsa-<cluster_id>. <cluster_id> indicates the ID of your cluster.
Work with RRSA
After you enable RRSA for your cluster, perform the following steps to enable the applications in the cluster to obtain STS tokens through RRSA. The STS tokens are used to call the APIs of specific cloud services.
Use a new RAM role and grant the required permissions to the RAM role
If you want to use an existing RAM role, you must grant the required permissions to the RAM role.
In this example, an application is created and RRSA is enabled for the cluster to allow the application to perform the following operations: assuming a specified RAM role and then calling an API operation to query clusters that belong to the current Alibaba Cloud account. The following resources are used.
Namespace: rrsa-demo
Service account: demo-sa
RAM role: demo-role-for-rrsa
Create a RAM role named demo-role-for-rrsa.
Use an Alibaba Cloud account to log on to the RAM console.
In the left-side navigation pane, choose . On the Roles page, click Create Role.
In the Create Role panel, click Switch To Editor to create a role.
For example, if you use Visual Editor, configure the role based on the following information and click OK.
Configuration item
Description
Effect
The default value is Allow.
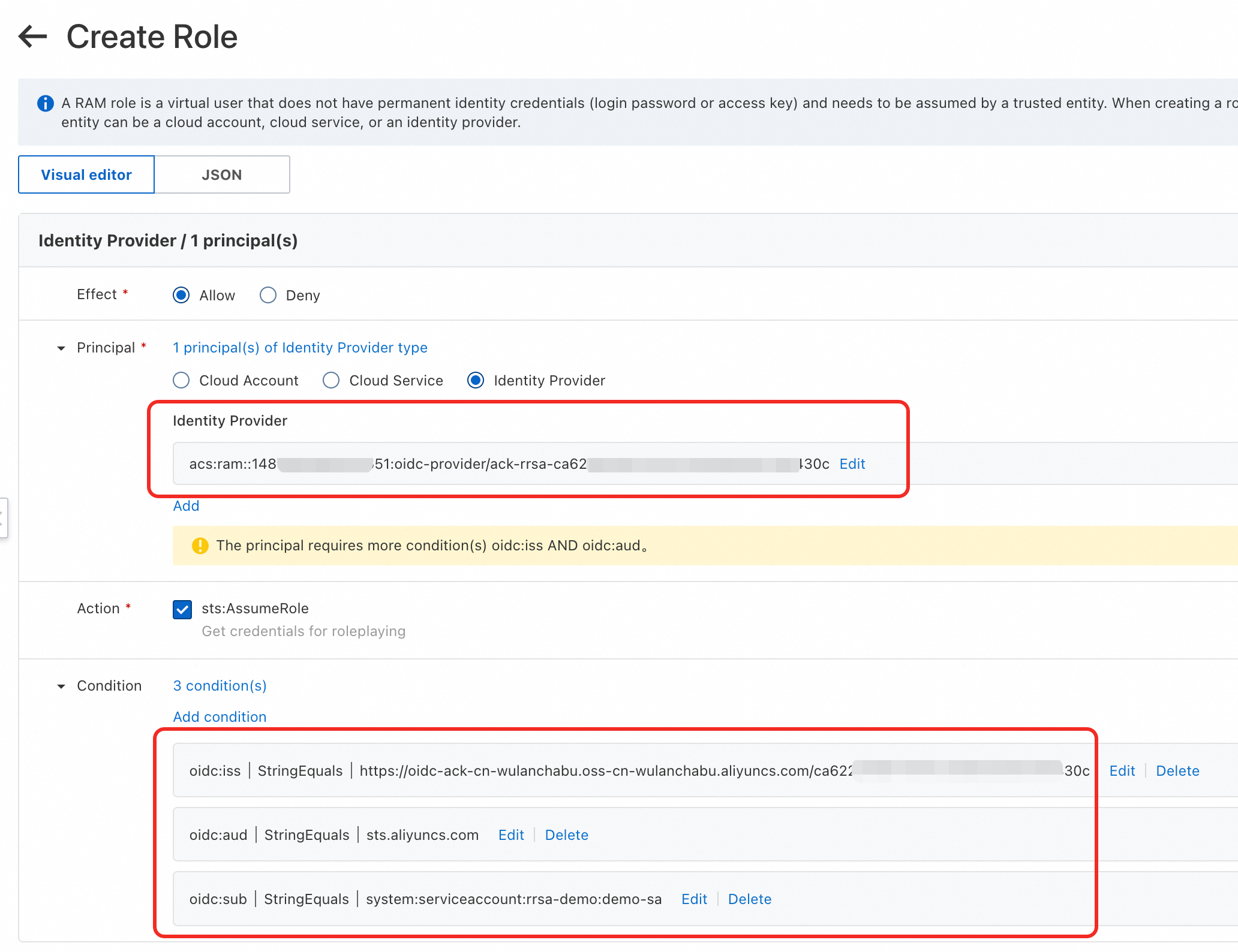
Principal
Select Identity Provider and click Edit.
Set the identity provider type to OIDC and select the identity provider of the cluster, such as ack-rrsa-<cluster_id>. <cluster_id> is the ID of your cluster.
Action
sts:AssumeRole is selected by default.
Condition
oidc:iss: This condition is automatically added after you select Identity Provider. Keep the default value.
oidc:aud: This condition is automatically added after you select Identity Provider. Keep the default value.
oidc:sub: You need to manually Add A Condition.
Condition Key:
oidc:subOperator:
StringEqualsCondition Value: The format is system:serviceaccount:<namespace>:<serviceAccountName>.
<namespace>: Specify the namespace of the application.
<serviceAccountName>: Specify the name of the service account.
In this example, enter
system:serviceaccount:rrsa-demo:demo-sa.
In the dialog box that appears, enter the role name
demo-role-for-rrsaand click OK.
Attach the AliyunCSReadOnlyAccess system policy to the created role. For more information, see Grant permissions to a RAM role.

Deploy the application.
Create a file named demo.yaml based on the following requirements:
NoteModify the following fields in the preceding template:
Replace
<role_arn>with the ARN of the RAM role that is used by the application. You can view the ARN on the Basic Information tab of the RAM console.Replace
<oid_provider_arn>with the ARN of the OIDC provider used by the cluster. You can move the pointer over Enabled to the right of RRSA OIDC on the Basic Information tab of the Cluster Information page.
Run the following command to deploy the application:
kubectl apply -f demo.yamlAfter the application is deployed, the program of the application can use the OIDC token, ARN of the RAM role, and ARN of the OIDC identity provider to call the STS AssumeRoleWithOIDC API operation to obtain the temporary STS token of the RAM role. Then, it can use the token to call the APIs of cloud services. For more information, see AssumeRoleWithOIDC.
Run the following command to print the log of the application:
kubectl -n rrsa-demo logs demoA list of clusters are displayed in the output:
20**/**/** 08:35:23 ======= [begin] list ACK clusters with RRSA ======= clusters: cluster id: cf***, cluster name: foo* cluster id: c8***, cluster name: bar* cluster id: c4***, cluster name: foob* 20**/**/** 08:35:24 ======= [end] list ACK clusters with RRSA =======Optional: Detach the AliyunCSReadOnlyAccess system policy from the RAM role. For more information, see Remove permissions from a RAM role.
Wait 30 seconds and run the following command to print the log of the application again:
kubectl -n rrsa-demo logs demoThe following error message indicates that the application does not have the required permissions:
20**/**/** 10:09:33 ======= [begin] list ACK clusters with RRSA ======= 20**/**/** 10:09:33 SDKError: StatusCode: 403 Code: StatusForbidden Message: code: 403, STSToken policy Forbidden for action cs:DescribeClusters request id: XXXX Data: {"accessDeniedDetail":{"AuthAction":"cs:DescribeClusters","AuthPrincipalDisplayName":"demo-role-for-rrsa:ack-ram-tool","AuthPrincipalOwnerId":"XXXX","AuthPrincipalType":"AssumedRoleUser","EncodedDiagnosticMessage":"XXXX","NoPermissionType":"ImplicitDeny","PolicyType":"ResourceGroupLevelIdentityBasedPolicy"},"code":"StatusForbidden","message":"STSToken policy Forbidden for action cs:DescribeClusters","requestId":"XXXX","status":403,"statusCode":403}
Use an existing RAM role and grant the required permissions to the RAM role
If you want the application to use an existing RAM role, you must modify the trust policy of the RAM role based on the following template. This way, the application can use the service account to assume the RAM role and obtain an STS token. For more information, see Edit the trust policy of a RAM role.
Example of the Statement configurations:
Modify the following fields in the Statement configurations:
Replace
<oidc_issuer_url>with the URL of the OIDC provider used by the cluster. On the Basic Information tab of the Cluster Information page, move the pointer over Enabled to the right of RRSA OIDC.Replace
<oidc_provider_arn>with the ARN of the OIDC provider used by the cluster. On the Basic Information tab of the Cluster Information page, move the pointer over Enabled to the right of RRSA OIDC.Replace
<namespace>with the namespace of the application.Replace
<service_account>with the service account used by the application.
{
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"oidc:aud": "sts.aliyuncs.com",
"oidc:iss": "<oidc_issuer_url>",
"oidc:sub": "system:serviceaccount:<namespace>:<service_account>"
}
},
"Effect": "Allow",
"Principal": {
"Federated": [
"<oidc_provider_arn>"
]
}
}Related documents
Some Alibaba Cloud SDKs allow applications to call the APIs of specific cloud services by using the OIDC tokens of RRSA. The following table describes the supported SDK versions and demos.
Programming language
Supported SDK version
Demo
Go
Alibaba Cloud Credentials for Go 1.2.6 and later
Java
Alibaba Cloud Credentials for Java 0.2.10 and later
Python 3
Alibaba Cloud Credentials for Python 0.3.1 and later
Node.js and TypeScript
Alibaba Cloud Credentials for TypeScript/Node.js 2.2.6 and later
Query a STS token to assume a RAM role during role-based SSO by calling AssumeRoleWithOIDC.